Search the Community
Showing results for tags 'security'.
-

Chrome extensions - Discovery of a Massive Surveillance Campaign
GHARIB posted a topic in Technology
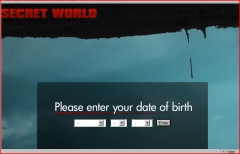
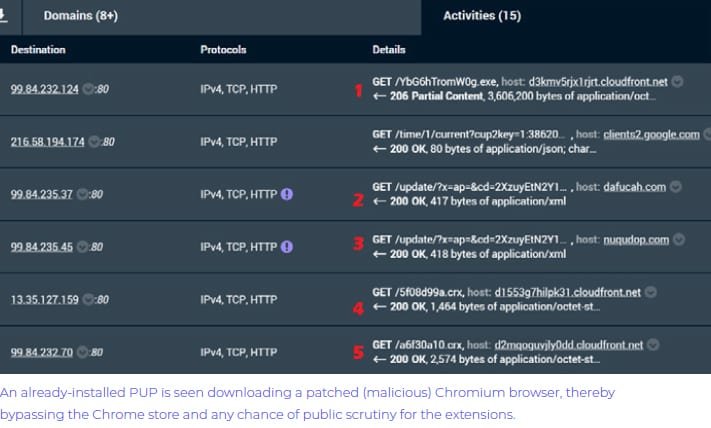
HIGHLIGHTS: - More than 33 million downloads - 111 malicious or fake Chrome extensions (from the GOOGLE Official Store - removed in JUNE 2020) - 15,160 malicious/suspicious domains MILLIONS of Google Chrome users may have had their intimate web browsing history hacked as security experts discover malicious spyware extensions, which have been downloaded more than 30 million times. Exemple of FAKE extension (infected): Discovered by Awake Security Team, these 3 months they have harvested 111 malicious or fake Chrome extensions using GalComm domains for attacker command and control infrastructure and/or as loader pages for the extensions. These extensions can take screenshots, read the clipboard, harvest credential tokens stored in cookies or parameters, grab user keystrokes (like passwords), etc. After analyzing more than 100 networks across financial services, oil and gas, media and entertainment, healthcare and pharmaceuticals, retail, high-tech, higher education and government organizations, Awake discovered that the actors behind these activities have established a persistent foothold in almost every network. Fortunately, these were live until May 2020 when they were finally reported to Google by the researchers and got removed from the Chrome store. For further information: https://awakesecurity.com/white-papers/the-internets-new-arms-dealers-malicious-domain-registrars/ -
Discord security advice Since server raiding and scam links are increasing, we are also increasing the security into our Discord server Terminology ‘Raid’ ‘Raider’ - A raid is where a large number of users will join a server with the express intention of causing issues for the server. A raider is an account engaging in this activity. 'Self-bot' - A self bot is an account that’s being controlled via custom code or tools. This is against Discord’s TOS. In the context of raids and moderation, these accounts are automated to spam, bypass filters or engage in other annoying activities. 'Phishing scam link' - Phishing scam link is a fraudulent ("spoofed") message/link sent by an attacker to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. How do detect malicious links ? First of all, never click on links that are send from people that are untrusted ! The most obvious way to find out if a link is a fraudulent link is to look at why the link was sent to you : Someone sends you a link, do I know this person ? If someone sends you a link that you didn't ask for, why is that person sending it to you ? If someone offers you free items (giveaway/lottery) by clicking on the link, what does this person gain by giving you this items ? Why would an "official" discord account advertise by message and not by mail? A person will never send you a gift without a reason, especially if you don't know them It is also important to check the url, and especially the domain name ! If a so-called official link from discord is sent to you, check that the link is from discord.com Check carefully the domain name. In general, characters are exchanged or are added (exemple discord => discorde, dlscord, discorb, ...) Check carefully the extension (suffix) of the domain name. In general, a commercial site will end with .com, if it is something else, be careful (exemple discord.com => discord.net, ...) Exemple of phishing link : How to report malicious links ? Report the user to Staff+ members so that they ban the member from the discord server Please always take a screenshot when doing the report Report by private message Report by contact-us if nobody answer Report the user to discord by using the report button (optional) Report the link to Google without clicking on it so that when people go there, they get a warning page : https://safebrowsing.google.com/safebrowsing/report_phish/ What to do if I click on a malicious link ? Change your Discord password If attacker already changed your password Try to change your password with the forgotten password feature Open a ticket into Discord support : https://support.discord.com Open a contact-us so that we can block the stolen account It's important to report your account to us with our contact-us because your account is trusted by other members. If your account send phishing to other members, there is more chance that they click on it since it's a "friendly" account ! What did Fearles Assassins added to discord to improve your security ? We have added a mandatory verification system for all newcomers. When a user joins the Discord server, the user receives a message with a reCAPTCHA that must be validated. We use for the verification : Cloudflare security Verify browser integrity Verify that the ip is not a known bot Verify that the ip is not a Tor ip Avoid DDOS / website exploit Google reCAPTCHA Verify that the user is not a bot Do not hesitate to ask us questions or to send us suggestions to improve security
-
This appeared on an Opera updates page that opened for me. I don't really know if this really a valid test or just an "always use Opera" sort of thing. I will have to try it with my other browsers, via Private-Incognito type modes. https://cryptojackingtest.com 1) I just tried it with IE 11 and the test-page said "protected", BUT my Norton AV said that it blocked a intrusion attempt by a a JSCoinminer site and a coinhive IP. 2) Tested on Chrome and Norton said that it blocked a JSCoinminer site before I even pressed "start" for the test...which said that my Chrome is "protected." 3) Tested on Edge and got the same as #2 above. I guess that my test is not valid because of the "interference" from Norton AV. BTW, I had used a free-proxy each time so that they could not connect my tests via my IP. 4) I ran the test on Opera and Norton did not react at all. The result was also "protected". That might imply that my IE, Chrome and Edge are not internally protected. " Other desktop users overall test results " 78.5% Protected 21.5% Not protected ++ Finished testing after Xernicus had replied below...
- 2 replies
-
- 1
-

-
- cryto
- crypto-currancy
-
(and 4 more)
Tagged with:
-
This site says that MS will install Emergency Updates today, at 5pm EST and 2pm PST...I just received mine at 1pm PST. It included updates for ARM and Windows Server 2016. https://www.theverge.com/2018/1/3/16846784/microsoft-processor-bug-windows-10-fix NOTE: "The update will also be available for older and supported versions of Windows today, but systems running operating systems like Windows 7 or Windows 8 won’t automatically be updated through Windows Update until next Tuesday. Windows 10 will be automatically updated today." Nest Tuesday is the traditional "Patch Tuesday". Here is the Update Catalog that I received for Win10 ver. KB4056892 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4056892 only about half apply to my win10 pro 64-bit ver.1709 Here is a PC Gamer article which says that the Intel CPU design problem won't affect gaming : http://www.pcgamer.com/serious-intel-cpu-design-flaw-may-require-a-windows-patch-but-probably-wont-affect-gaming-performance/?utm_content=buffer5f93b&utm_medium=social&utm_source=facebook&utm_campaign=buffer-maxpcfb The biggest danger is to large companies with large sites and systems. "... the fixes will also rely on firmware updates from Intel, AMD, or other vendors that are rolling out...."
-
Hallo! With the growing security concern via the net, I thought I'd share my security tips,etc and how ive secured my PC w/o $$ and so far, so good. Maybe others can contribute their knowledge/wisdom. I was watching youtube and saw all the "web analytics" blocked in the site (see blocking) Good old Kaspersky I.S. I recommend, built in browser protection, I have a trial reset, G2G. Also, I cant emphasize enough, use a host file(see block2) block imbedded ads, if you really wanna get technical, clear browser cookies, visit a site, and then check options/remove individual cookies and see what othe sites are connecting to you. (Mozilla) Ive added individual ads to my hostfile blocklist Oh, I stay away from IE. Derp! P2p, use peer block, maybe VPN, definitely have: Spybot, Spywareblaster, Malwarebytes, CCleaner, or some utility, Ive tested othe antimalware progs, Ive found some things, here and there, but my install is over 3yrs old, still good. I boot up in like 1:20s. EVGA 122-CK-NF68-AR LGA 775 NVIDIA nForce 680i SLI ATX Intel MotherboardIntel Pentium D 3.4Ghz 4Gig Ram, Win7 32bit Geforce 210 Pc is like 8 yrs old, lol. Becoming a classic, So, what you workin with?
-
Email and phone scams claiming to be the Windows 10 upgrade "... cybercriminals are trying to capitalize on the great momentum of Windows 10, with nefarious email, web, and phone scams directing our customers to install ransomware and other malware." more here: https://support.microsoft.com/en-us/kb/3086823 Warn your less-knowledgeable friends and relatives!
- 1 reply
-
- 1
-

-
- security
- windows 10
-
(and 1 more)
Tagged with:
-
There's a way to compromise a home network without actually being on it. It's called "cross-site request forgery." It starts by redirecting a user to a malicious website, typically by phishing. The site uses the prey's browser to send requests to the home router. The router thinks the prey is sending the requests from the home network. "Home routers are very naive," said Incapsula's Ofer Gayer. Most consumers pay as much attention to routers as they do to doorknobs. That's not the case with Net marauders. They're finding the devices ripe targets for mischief. "We've seen a big increase in malware designed for home routers," said Incapsula researcher Ofer Gayer. "Every week, we see a new vulnerability in a vendor's routers," he told TechNewsWorld. "They're low-hanging fruit if you're a hacker. They're a very soft target." Home routers are the soft underbelly of the Internet, observed Andrew Conway, a threat researcher at Cloudmark. "They were never designed to be high security components, and once they are installed, they are typically never updated," he told TechNewsWorld. "Even when vulnerabilities are discovered, a vendor may not patch their firmware -- and if they do, the patches are rarely applied," Conway said. Cross-Site Shenanigans As soft a target as routers may be, they have been protected by a restriction on how their settings can be altered. Typically, you have to be on a network locally before you can access and change those settings. That's not always the case, though, as Incapsula recently pointed out. Incapsula discovered one router maker had installed what was essentially a backdoor in its products to make it easier to service the routers. Unfortunately, Net miscreants discovered what the router maker had done, and they began herding many of the routers together to mount distributed denial-of-service attacks. "Routers are strong enough today to create a pretty significant denial-of-service attack," Gayer said. Even if your router maker doesn't put a backdoor in your router, there's a way to compromise a home network without actually being on it. It's called "cross-site request forgery." It starts by redirecting a user to a malicious website, typically by some kind of phishing email. The site uses the prey's browser to send requests to the home router. The router thinks the prey is sending the requests from the home network. "Home routers are very naive," Gayer explained. Once a predator opens up the channel between the prey's browser and the router, a host of options become available. "I can change whatever I want," Gayer noted. "I can change the DNS server. I can open a hole in the firewall. I can change the admin password." To do all that, no access to the router is needed. "I just make you perform the requests by redirecting you," Gayer said. Targeting Uncle Sam Last week wasn't the best of times for federal employees. The decibel level of the furor over the Office of Personnel Management data breach continued to rise. It didn't take long for signs to appear that Net bandits were putting the stolen data to use. For example, an Army base in Alabama warned its employees of a phishing email purporting to be from the OPM and directing targets to a website where personal information could be cajoled from them. Meanwhile, OneWorldLabs, which monitors the Dark Net, spotted data apparently from the OPM breach for sale. If that were the case, though, it would throw cold water on the idea that the Chinese government was behind the OPM break-in, since it likely would keep the data under wraps and not be trying to sell it to cybercriminals. Nevertheless, most of the U.S. finger-pointing has been toward Beijing. "China would like to be in every U.S. system on some level," said Jared DeMott, principal security researcher at Bromium. "The data the hackers stole could just be the initial phase of the attack, while moving toward more attractive targets," he told TechNewsWorld. What makes matters worse is that there's little the United States can do about the breach, said Securonix Chief Scientist Igor Baikalov. "First of all, the U.S. spies for 'national security advantages' just like China does -- no moral high ground for he U.S. there," he told TechNewsWorld. "Second and most frustrating, there's not much the U.S. can do to retaliate for this attack," Baikalov said. "Economic sanctions? They're hardly applicable to the country that holds most of your national debt." Source http://www.technewsworld.com/
-
Symantec says a critical vulnerability within some Apple Mac models could allow hackers to inject systems with persistent rootkit malware. Cyberattackers could, in theory, reflash the computer's firmware and install Extensible Firmware Interface (EFI) rootkit malware. The security firm confirmed the existence of the security flaw late on Thursday. The flaw, called the Apple Mac OS X EFI Firmware Security Vulnerability, was originally disclosed May 29 by Apple's security researcher Pedro Vilaca. The problem lies within Mac sleep mode. After Macs awake from this low-power hibernation, a flawed suspend-resume implementation means that some Mac models' flash protections are left unlocked. Virulent malware, such as the EFI rootkit, can be used to remotely control a system and potentially steal user data -- and may not be eradicated even if a system wipe is set in motion. But while this attack is unlikely to impact on users en masse, it could be exploited in order to spy upon specific, targeted users with valuable data or accounts to share. This is not the only Apple-related security flaw to hit the headlines this year. In March, Apple released a patch to protect iOS users from FREAK, a decade-old bug which left users of Apple's Safari and Google Android browsers vulnerable to hacking through a forced downgrade of encryption protocols. Symantec has confirmed the existence of the vulnerability and has rated the flaw as "critical" as it can provide "an attacker with persistent root access to a computer that may survive any disk wipe or operating system reinstallation," according to the firm. "The vulnerability could be remotely exploited by an attacker if used in conjunction with another exploit that provided root access," Symantec said. "While such vulnerabilities are not widespread, they do emerge from time to time. Once an attacker has root access, the only condition required for successful exploit is that the computer enter sleep mode." Vilaca claims the bug can be used with Safari or another remote vector to install an Extensible Firmware Interface (EFI) rootkit without physical access, and the only requirement is that the computer is suspended within the session. To date, Symantec has tested four different Mac computer models. The security firm found that the Mac Mini 5.1 and MacBook Pro 9.2 are vulnerable, whereas the MacBook Pro 11.3 and MacBook Air 6.2 are not affected. Vilaca's tests verified the MacBook Pro Retina 10.1, MacBook Pro 8.2, MacBook Air 5.1 and Mac Pro 9.1 are vulnerable. All computers tested ran on Apple's latest firmware versions. Vilaca commented: "I'm pretty sure Apple is aware of the bug or at least it would be quite irresponsible for them to not test if their BIOS implementation was vulnerable to the Dark Jedi attack. I had no issues doing PoC tests with it but definitely needs other people to test it out (at least to find which other Macs are vulnerable)." Until Apple issues a firmware patch to fix the security flaw, concerned users are advised to shut down their computers rather than put them in sleep mode. This story originally posted as "Symantec confirms existence of unpatched rootkit Mac security flaw" on ZDNet. Source http://www.cnet.com/
-
I received this email today: Keep Your ID and Accounts Safe March 2015 Dear Bone-Head, In the last several years, scammers have increased their "phishing" attempts (e-mails asking individuals to divulge sensitive information). Financial Center has learned about a new phishing scam that is currently circulating the Web, and wanted to pass the information along to you so you and your family can stay safe. The Scam The National Credit Union Administration (NCUA) has issued a warning to consumers about a website with a logo and design that is similar to the NCUA's site. Under the name of 'National Credit Union', phishers are attempting to convince consumers to provide personal information or send money to the fake organization. Some consumers have also received emails from the imposter website. The site originates in Australia and claims to offer services in the US, Europe and the Commonwealth of Independent States. Please know this website is not affiliated with the NCUA and the emails are not from the NCUA. What You Can Do to Stay Safe Here are some preventive actions you can take to help safeguard you and your family from falling victim to these types of scams: 1. Use caution with e-mails containing links and attachments. 2. Never send sensitive information through e-mail; especially in response to an unsolicited e-mail. 3. Do not follow Web links in unsolicited e-mails from apparent federal banking agencies; instead, bookmark or type the agency's Web address in your preferred Web browser. 4. Keep your anti-virus software up-to-date and running. 5. Keep your operating system and applications up-to-date with the latest patches directly from the manufacturer If You Think You are a Victim of the NCUA Phishing Scam If you receive an email claiming to be the NCUA, the federal agency has asked consumers to call the NCUA's Fraud Hotline toll-free at 800-827-9650. You can also contact the Internet Crime Complaint Center, which is a partnership between the FBI and the National White Collar Crime Center. Identity theft victims are also encouraged to alert their financial institutions, as well as place a fraud alert on their credit reports. You can place a fraud alert by contacting one of the three major credit bureaus; they are reachable at: Equifax 800-525-6285, Experian 888-397-3742 and TransUnion 800-680-7289. Sincerely, BURT Financial Center Credit Union "Bone-Head" is my edit
-
I've been getting PayPal phishing emails every two weeks recently. Paypal says they will always address you by your first and last name, and I say that they will never have a little tab for you to click to log onto their site. (I have hovered my mouse pointer over such tabs and the address shown at the bottom of the browser is never to Paypal.com) Forward any suspicious emails to spoof@paypal.com Ironically the reply-to: and from: in this latest attempt were for "security . org", to whom I also forwarded the email. It nothing else, it will help them understand if they ever get thousands of replies from Mailer-Daemons, like I did one time, saying that the address sent to was invalid. Quote from part of the PayPal auto-reply to my forwarded message: Paypal Will Always:- Address our customers by their first and last name or business name oftheir PayPal account Paypal Will Never:- Send an email to: "Undisclosed Recipients" or more than one email address- Ask you to download a form or file to resolve an issue- Ask in an email to verify an account using Personal Information such as Name, Date of Birth, Driver's License, or Address- Ask in an email to verify an account using Bank Account Information such as Bank Name, Routing Number, or Bank Account PIN Number- Ask in an email to verify an account using Credit Card Information such as Credit Card Number or Type, Expiration Date, ATM PIN Number, or CVV2 Security Code- Ask for your full credit card number without displaying the type of card and the last two digits- Ask you for your full bank account number without displaying your bankname, type of account (Checking/Savings) and the last two digits- Ask you for your security question answers without displaying each security question you created- Ask you to ship an item, pay a shipping fee, send a Western Union Money Transfer, or provide a tracking number before the payment receivedis available in your transaction historyREAD!Any time you receive an email about changes to your PayPal account, the safest way to confirm the email's validity is to log in to your PayPal account where any of the activity reported in the email will be available to view. DO NOT USE THE LINKS IN THE EMAIL RECEIVED TO VISIT THE PAYPAL WEBSITE. Instead, enter www.paypal.com into your browser to log in to your account.What is a phishing email?You may have received an email falsely claiming to be from PayPal or another known entity. This is called "phishing" because the sender is "fishing" for your personal data. The goal is to trick you into clickingthrough to a fake or "spoofed" website, or into calling a bogus customerservice number where they can collect and steal your sensitive personal or financial information.We will carefully review the content reported to us to certify that the content is legitimate. We will contact you if we need any additional information for investigating the matter. Please take note to the security tips provided above as they may help to answer any questions that you may have about the email you are reporting to us. Help! I responded to a phishing email!If you have responded to a phishing email and provided any personal information, or if you think someone has used your account without permission, you should immediately change your password and security questions.You should also report it to PayPal immediately and we'll help protect you as much as possible. 1. Open a new browser and type in www.paypal.com. 2. Log in to your PayPal account. 3. Click "Security and Protection" near the top of the page. 4. Click "Identify a problem." 5. Click "I think someone may be using my account without permission." 6. Click "Unauthorized Account Activity."Thank you for your help making a difference.Every email counts. By forwarding a suspicious-looking email to spoof@paypal.com, you have helped keep yourself and others safe from identity theft. Thanks, The PayPal Team
-
Apple Inc. said it plans additional steps to keep hackers out of user accounts but denied that a lax attitude toward security had allowed intruders to post nude photos of celebrities on the Internet. In his first interview on the subject, Apple Chief Executive Tim Cook said celebrities' iCloud accounts were compromised when hackers correctly answered security questions to obtain their passwords or when they were victimized by a phishing scam to obtain user IDs and passwords. He said none of the Apple IDs and passwords leaked from the company's servers. To make such leaks less likely, Mr. Cook said Apple will alert users via email and push notifications when someone tries to change an account password, restore iCloud data to a new device or when a device logs into an account for the first time. Until now, users got an email when someone tried to change a password or log in for the first time from an unknown Apple device; there were no notifications for restoring iCloud data. Apple said it plans to start sending the notifications in two weeks. It said the new system will allow users to take action immediately, including changing the password to retake control of the account or alerting Apple's security team. But Mr. Cook said the most important measures to prevent future intrusions might be more human than technological. In particular, he said Apple could have done more to make people aware of the dangers of hackers trying to target their accounts or the importance of creating stronger and safer passwords. "When I step back from this terrible scenario that happened and say what more could we have done, I think about the awareness piece," he said. "I think we have a responsibility to ratchet that up. That's not really an engineering thing." Asked about the criticism that Apple hadn't focused enough on the security of its products, Mr. Cook pointed to the company's work with Touch ID, the fingerprint sensor in its iPhone 5S that unlocks the phone and authorizes purchases. He also said Apple will broaden its use of an enhanced security system known as "two-factor authentication," which requires a user, or a hacker, to have two of three things to access an account: a password, a separate four-digit one-time code or a long access key given to the user when they signed up for the service. When the feature is turned on, Apple requires users to complete two of those steps to sign into an iTunes account from a new device. As part of the next version of its iOS mobile-operating system, due out later this month, the feature will also cover access to iCloud accounts from a mobile device. Apple said a majority of users don't use two-factor authentication, so it plans to more aggressively encourage people to turn it on in the new version of iOS. If the celebrities had the system in place, hackers wouldn't have had an opportunity to guess the correct answer to security questions, Apple said. Outside security experts said Apple had made it too easy for hackers to access users' information, by requiring only the answer to two security questions. Particularly for celebrities, such answers can be guessed by outsiders. "There's a well-understood tension between usability and security," said Ashkan Soltani, an independent security researcher who has worked with The Wall Street Journal in the past. "More often than not, Apple chooses to err on the side of usability to make it easier for the user that gets locked out from their kid's baby photos than to employ strong protections for the high-risk individuals." He said the new notifications "will do little to actually protect consumers' information since it only alerts you after the fact." Apple said it is working with law enforcement to investigate the incident and identify the hackers. A spokesman declined to specify how many users' accounts had been compromised, citing the continuing investigation. "We want to do everything we can do to protect our customers, because we are as outraged if not more so than they are," said Mr. Cook. Apple is battling to preserve its reputation for looking after its users ahead of a major product announcement next week. The company is facing the type of negative publicity that it usually has managed to avoid, a situation magnified by the popularity of the victims. Nude photos of actress Jennifer Lawrence and a host of other celebrities started spilling onto the Internet last week, raising concerns about the security of Apple's online services. Apple users can back up photos, music and other data onto its iCloud service. via: http://online.wsj.com/articles/tim-cook-says-apple-to-add-security-alerts-for-icloud-users-1409880977
-
Every Android application has its own unique identity, typically inherited from the corporate developer’s identity. The Bluebox Security research team, Bluebox Labs, recently discovered a new vulnerability in Android, which allows these identities to be copied and used for nefarious purposes. Dubbed “Fake ID,” the vulnerability allows malicious applications to impersonate specially recognized trusted applications without any user notification. This can result in a wide spectrum of consequences. For example, the vulnerability can be used by malware to escape the normal application sandbox and take one or more malicious actions: insert a Trojan horse into an application by impersonating Adobe Systems; gain access to NFC financial and payment data by impersonating Google Wallet; or take full management control of the entire device by impersonating 3LM. Implications: This is a widespread vulnerability dating back to the January 2010 release of Android 2.1 and affecting all devices that are not patched for Google bug 13678484, disclosed to Google and released for patching in April 2014. All devices prior to Android 4.4 (“KitKat”) are vulnerable to the Adobe System webview plugin privilege escalation, which allows a malicious application to inject Trojan horse code (in the form of a webview plugin) into other apps, which leads to taking control of the entire app, all of the apps’s data, and being able to do anything the app is allowed to do. Android 4.4 is vulnerable to Fake ID, but not specifically to the Adobe System webview plugin due to a change in the webview component (the switch from webkit to Chromium moved away from the vulnerable Adobe-centric plugin code). Users of devices from specific vendors that include device administration extensions are at risk for a partial or full device compromise by malware. The 3LM device extensions (temporarily owned by Motorola and Google) are present in various HTC, Pantech, Sharp, Sony Ericsson, and Motorola devices – and are susceptible to the vulnerability as well. Other devices and applications that depend upon the presence of specific signatures to authenticate an application may also be vulnerable. Essentially anything that relies on verified signature chains of an Android application is undermined by this vulnerability. How it works: Android applications are typically cryptographically signed by a single identity, via the use of a PKI identity certificate. The use of identity certificates to sign and verify data is commonplace on the Internet, particularly for HTTPS/SSL use in web browsers. As part of the PKI standard, an identity certificate can have a relationship with another identity certificate: a parent certificate (“issuer”) can be used to verify the child certificate. Again, this is how HTTPS/SSL works – a specific web site SSL certificate may be issued by a certificate authority such as Symantec/Verisign. The web site SSL certificate will be “issued” by Verisign, and Verisign’s digital identity certificate will be included with the website certificate. Effectively, the web browser trusts any certificate issued by Verisign through cryptographic proof that a web site SSL certificate was issued by Verisign. Android applications use the same certificate signature concepts as SSL, including full support for certificates that are issued by other issuing parties (commonly referred to as a “certificate chain”). On an Android system, the digital certificate(s) used to sign an Android application become the application’s literal package “signature”, which is accessible to other applications via normal application meta-data APIs (such as those in PackageManager). Application signatures play an important role in the Android security model. An application’s signature establishes who can update the application, what applications can share it’s data, etc. Certain permissions, used to gate access to functionality, are only usable by applications that have the same signature as the permission creator. More interestingly, very specific signatures are given special privileges in certain cases. For example, an application bearing the signature (i.e. the digital certificate identity) of Adobe Systems is allowed to act as a webview plugin of all other applications, presumably to support the Adobe Flash plugin. In another example, the application with the signature specified by the device’s nfc_access.xml file (usually the signature of the Google Wallet application) is allowed to access the NFC SE hardware. Both of these special signature privileges are hard coded into the Android base code (AOSP). On specific devices, applications with the signature of the device manufacture, or trusted third parties, are allowed to access the vendor-specific device administration (MDM) extensions that allow for silent management, configuration, and control of the device. Overall, this is an appropriate use of digital signatures in a system that supports the notion of PKI digital certificate identities. However, Bluebox Labs discovered a vulnerability that has been relatively present in all Android versions since Android 2.1, which undermines the validity of the signature system and breaks the PKI fundamental operation. The Android package installer makes no attempt to verify the authenticity of a certificate chain; in other words, an identity can claim to be issued by another identity, and the Android cryptographic code will not verify the claim (normally done by verifying the issuer signature of the child certificate against the public certificate of the issuer). For example, an attacker can create a new digital identity certificate, forge a claim that the identity certificate was issued by Adobe Systems, and sign an application with a certificate chain that contains a malicious identity certificate and the Adobe Systems certificate. Upon installation, the Android package installer will not verify the claim of the malicious identity certificate, and create a package signature that contains the both certificates. This, in turn, tricks the certificate-checking code in the webview plugin manager (who explicitly checks the chain for the Adobe certificate) and allows the application to be granted the special webview plugin privilege given to Adobe Systems – leading to a sandbox escape and insertion of malicious code, in the form of a webview plugin, into other applications. The problem is further compounded by the fact that multiple signers can sign an Android application (as long as each signer signs all the same application pieces). This allows a hacker to create a single malicious application that carries multiple fake identities at once, taking advantage of multiple signature verification privilege opportunities to escape the sandbox, access NFC hardware used in secure payments, and take device administrative control without any prompt or notification provide to the user of the device. For the PKI & code savvy, you can see for yourself in the createChain() and findCert() functions of the AOSP JarUtils class – there is a conspicuous absence of cryptographic verification of any issuer cert claims, instead defaulting to simple subjectDN to issuerDN string matching. An example of the Adobe Systems hardcoded certificate is in the AOSP webkit PluginManager class. Source: https://bluebox.com/blog/technical/android-fake-id-vulnerability/
-
So over the past month I have had 2 different credit cards and a debit card incur an international charge of $49.50. All of them coming from a different fake websites setup to look like customer service sites. I googled one of the websites ( HCINCSUPPORT.COM ) and I am not the only one getting hit from this supposed company. After the first card was hit I thought it was a travel agents fault in their email security since i sent them my credit card info. So i just blew it off got a new card. A week later my second credit card was hit for the same charge. This past week my debit card was hit for the exact international charge from a phony website. I contacted the company and they told me I ordered some weight loss supplement and they even had my address with the order. I ran a malware bytes scan after the 2nd fraud charge and found 3 malware from an accidental install of a toolbar (incredibar ) and got rid of that. I used my debit card ( 3rd fraud charge) a day before i ran the scan so maybe they got the info? Does anyone have any recommendations on what I should do? Am I safe now that the malware has been removed? Was that the cause in the first place? I mean I have all new cards now and I have ran malware bytes and virus scans multiple times and they aren't coming up with anything now. Thanks for any information or advice.
-
From the album: Helper Pics
unexpected popup, probable source: xfire -
I've owned a mac for quite a while now. I'm just wondering whats the best/most useful antivirus/security programmes designed specifically for the Mac. I've used all the free ones from the apple store but never found them that great. You maybe wondering why I use them. Well to protect my mac as the threats of virus' have increased and to protect friends and family from windows virus' that I may have on my mac. So back to the original question what's the most useful?
-
Firstly, a little introduction to these tutorials. I am currently working on a clients website, and when I want to take a break, I've decided I will be posting about techniques I've used to cater for different needs, which people may find interesting. Today, I'll be showing you how you can easily protect your downloadable media. Why would you want to do this? Well, often we want to hide the location of the downloads, to stop people leeching your content. And most measures can be easily swerved. Here is a method I quite like. I have annotated everything for your convenience. Filename: download.php <?php $filename = "downloaded.zip"; // this is the fake name you want the downloaded file to be called. $source = "/downloads/thefile.zip"; // this is the real name and location of the file. if(file_exists($source)) { // check that the real file exists, if so do the following.. header('Content-type: application/zip'); // set the content type of the current page to the type of file being downloaded header('Content-Disposition: attachment; filename="'.$filename.'"'); // Forge the download name by setting filename= readfile($source); // grab the real file to prompt download. } else { // if the file doesn't exist echo "Error: File not found!"; // display error message } ?> So how do we use this? going to the destination: mysite.com/download.php would grab the file 'thefile.zip' from the /downloads/ folder, and prompt you to download it, but with a new name of 'downloaded.zip' This is the simplest version of this method. Obviously with use of $_GET requests you can have download.php choose varying files from the /downloads/ folder. Example below: Filename: download.php <?php $id = $_GET['file']; $filename = "downloaded-".$id.".zip"; // will forge the name downloaded-5.zip (if download.php?file=5 is requested) $source = "/downloads/thefile-".$id.".zip"; // will pick the real file titled thefile-5.zip (if download.php?file=5 is requested) if(file_exists($source)) { // check that the real file exists, if so do the following.. header('Content-type: application/zip'); // set the content type of the current page to the type of file being downloaded header('Content-Disposition: attachment; filename="'.$filename.'"'); // Forge the download name by setting filename= readfile($source); // grab the real file to prompt download. } else { // if the file doesn't exist echo "Error: File not found!"; // display error message } ?> It gets even more advanced once you start playing with more and more security. When dealing with premium ($$$) content, it's good to use a database and give all your files a masked name, by MD5 encoding the names, storing them in a database with an assigned ID, and having download.php retreive the filename from the database to know which file to retreive. But that'd look a little messy for this tutorial I hope you learned something by reading this.. Thanks for reading! Chuckun
About Us
We are glad you decided to stop by our website and servers. At Fearless Assassins Gaming Community (=F|A=) we strive to bring you the best gaming experience possible. With helpful admins, custom maps and good server regulars your gaming experience should be grand! We love to have fun by playing online games especially W:ET, Call of Duty Series, Counter Strike: Series, Minecraft, Insurgency, DOI, Sandstorm, RUST, Team Fortress Series & Battlefield Series and if you like to do same then join us! Here, you can make worldwide friends while enjoying the game. Anyone from any race and country speaking any language can join our Discord and gaming servers. We have clan members from US, Canada, Europe, Sri Lanka, India, Japan, Australia, Brazil, UK, Austria, Poland, Finland, Turkey, Russia, Germany and many other countries. It doesn't matter how much good you are in the game or how much good English you speak. We believe in making new friends from all over the world. If you want to have fun and want to make new friends join up our gaming servers and our VoIP servers any day and at any time. At =F|A= we are all players first and then admins when someone needs our help or support on server.








.thumb.png.bfaac282e96946b739dbbdf6794a004b.png)
.thumb.png.44adc66c5ae1f4f5de67efb0e0df1756.png)